Imagine sending a message across the world and trusting it will arrive perfectly intact. That’s the magic of TCP, or Transmission Control Protocol – a core technology keeping the internet running smoothly. From emails to videos, TCP ensures that data travels reliably across networks, accurately and in the right order. In this post, we’ll dive into TCP’s essential role, uncovering how it powers the internet’s backbone and keeps our digital world connected. Ready to explore the engine behind online communication? Let’s get started!
What is TCP/IP?
TCP and IP are two different communication protocols that complement each other’s functionality.
The Internet protocol or IP delivers (routes and addresses) data packets between a source (device or application) and their destination. It makes sure that those packets arrive at the right destination. It defines the rules and formats for applications and devices to communicate and exchange those data packets on a specific network or across different connected networks.
The transmission control protocol or TCP organizes data in a specific manner to protect them while exchanged between a client and a server. It’s a very used protocol on networks by all types of devices and applications. TCP protects data’s integrity from the sending and all the way to their delivery.
The development of these protocols (TCP/IP) happened in the 1970s. In that decade, the ARPANET became really popular, which motivated the creation of more networks to connect different organizations. Since those networks used a different protocol to send data back and forth, they could not communicate among them. The creation of a technology that could work as an intermediary to allow such communication became a need.
The combination of TCP and IP and its official adoption as the standard protocol -in 1983-for ARPANET (Internet’s predecessor) was the solution. No matter what other protocols networks used, if they supported TCP/IP, they could communicate with all the TCP/IP networks that existed.
The two technologies, TCP and IP, became the technical base for the modern Internet to operate and grow. Actually, here the word Internet emerged, meaning “an interconnected network of networks”.
How does it work?
IP protocol works through different rules and resources, like the IP addresses. To connect to the Internet, domains and devices get a unique IP address to be identified and allowed to communicate (exchange data) with other connected devices.
Data travel across networks separated into pieces (packets). Every piece gets IP information (IP address) attached for routers to read it and send the packet to the correct destination. Once there, the way for those packets to be handle will depend on the kind of protocol (commonly TCP or UDP) combined with the IP to transport them.
IP is a connectionless protocol. All data packets are just addressed, routed, and delivered without existing acknowledgment from the destination to the source. This lack is resolved through the Transmission Control Protocol.
TCP secures the travel and delivery of data packets across networks through a specific process. To start, a connection between the source and the destination is required, even before the transmission of data begins. This, because TCP is a connection-oriented protocol. To work properly, it needs to guarantee this active connection until the sending and receiving of data get completed.
When the communication begins, TCP takes the sender’s messages and chops them into packets. To protect messages’ integrity, TCP numbers every packet. Then packets are ready to go to the IP layer for being transported. They will be dispatched to travel around different routers and gateways of the network to reach their destination. No matter all the packets are part of the same message, they can have different routes to arrive at the same destination.
Once they all hit their destination, TCP proceeds to re-build the message by putting all their pieces (packets) together again to make a proper delivery.
This ideal scenario can be affected if networks face issues. Data packets could get lost in transit, duplicated, or disordered. The advantage is TCP’s functionality can detect such problems and fix them. The protocol can ask the lost packets to be re-sent to organize them again in the correct order. In case messages can’t be delivered, this is reported to the sender (source).
As you see, the Internet is a packet-switched network. All data are chopped into packets that are dispatched through lots of different routes simultaneously. When they finally hit their destination, they get re-built by TCP. And IP is in charge of the packets to be sent to the correct destination.
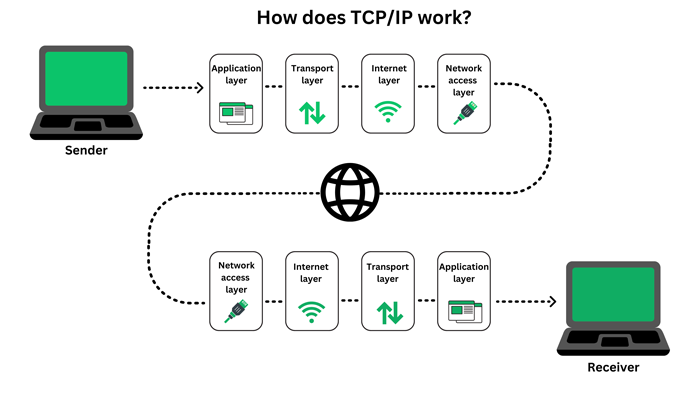
TCP/IP layers
TCP/IP’s most updated model includes the following four layers. All collaborate for the same purpose, the transmission of data.
- Application layer. This is the top layer, and it supplies an interface for applications and network services to communicate. It identifies participants involved in a communication, defines the access to the network’s resources, and the rules for application protocols and transport services interaction. Application layer includes all the higher-level protocols like DNS, HTTP, SSH, FTP, SNMP, SMTP, DHCP, etc.
- Transport layer. It defines the amount of data and the rate for transporting data correctly. It receives messages from the application layer, divides them into pieces, transports them, re-builds them following the proper sequence, and solves possible issues to guarantee their integrity and proper delivery. TCP operates in this layer.
- Internet layer. The internet layer, also known as the IP or network layer (not to be confused with the network access layer), is in charge of sending packets and ensuring that data is transferred as precisely as possible. As it controls the direction and pace of traffic, it is somewhat similar to a traffic controller on a road. Additionally, it supplies the procedural steps and functionalities for transferring data sequences. This layer’s protocols include IPv4, IPv6, ICMP, and ARP.
- Network access layer: The OSI model’s data link layer and physical layer are combined to form the network access layer. It outlines the process through which data is actually transferred over the network. It also covers how hardware components that physically interact with a network, such as twisted-pair copper wire, optical fiber, and coaxial cable, transmit data via optical or electrical means. The network access layer is the bottom layer in the TCP/IP model.
Understanding the TCP Handshake process
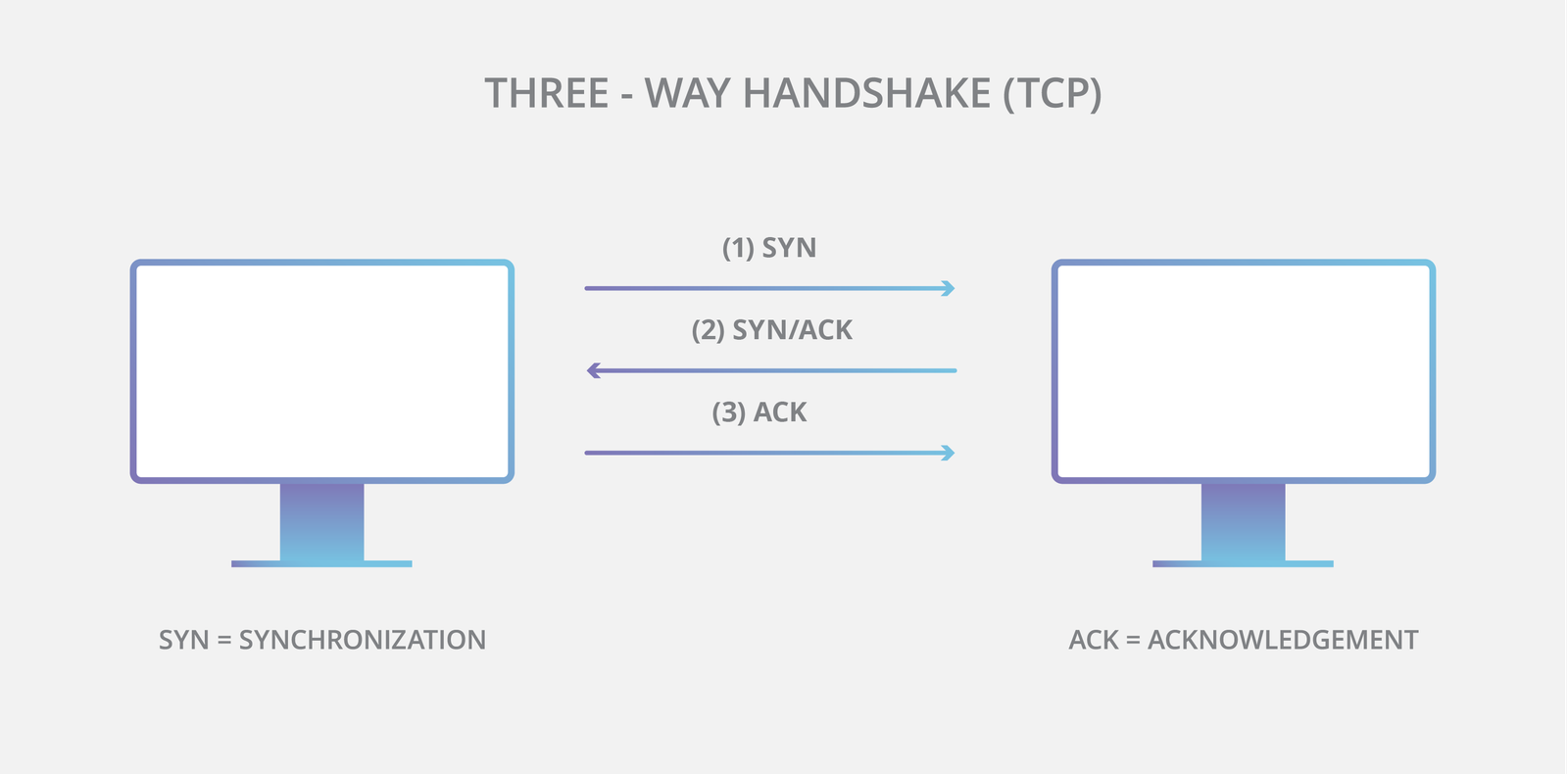
The primary version of IP used on the Internet today is Internet Protocol Version 4 (IPv4). Due to size constraints with the total number of possible addresses in IPv4, a newer protocol was developed. The newer protocol is called IPv6. It makes many more addresses available and is increasing in adoption.
Advantages of TCP/IP
- It allows connecting different kinds of devices.
- It makes possible cross-platform communications among diverse networks.
- It supports different protocols for routing.
- It offers high possibilities of scalability. You can add networks without causing trouble.
- It supplies IP addresses to devices for identifying them.
- It’s independent of the operating system.
- It’s an open protocol. No one owns it. Everybody can use it.
- It facilitates reliable communication through data packet retransmission in case of loss, ensuring data integrity.
- It offers robust error detection and correction capabilities, enhancing data transmission reliability.
Disadvantages of TCP/IP
- To replace protocols on TCP/IP is not simple.
- It doesn’t define clearly the concepts of services, protocols, and interfaces. It can be difficult to assign a category to new technologies included in modern networks.
- It works for wide networks. It’s not suitable for small ones (PAN or LAN).
- Susceptible to security vulnerabilities if not properly secured, making encryption and other security measures essential.
Comments (0)
Leave a Comment
No comments yet. Be the first to comment!